Fig. X. Single Sign-on, Third-Party Security Service
Oasis Security Services Use Cases And Requirements: Issues List
26 Feb 2001
This document catalogs issues with the requirements and use cases for the Security Assertions Markup Language (SAML) developed the Oasis Security Services Technical Committee.
The issues list presented here documents issues brought up in response to Use Case and Requirements drafts as well as other issues mentioned on the security-use and security mailing lists, in conference calls, and in other venues.
Each issue is formatted according to the proposal of David Orchard to the general committee:
ISSUE:[Document/Section Abbreviation-Issue Number: Short name]
Issue long description.
Possible resolutions, with optional editor resolution
Decision
The issues are informally grouped according to general areas of concern. For this document, the "Issue Number" is given as "#-##", where the first number is the number of the issue group.
The issues are in varying levels of resolution. Some are stated as questions or placeholders for further investigation. Others are stated as problems with resolutions, and still others have full-blown use case scenarios attached.
ISSUE:[UC-0-01:MergeUseCases] There are several use case scenarios in the Straw Man 1 that overlap in purpose. For example, there are several single sign-on scenarios. Should these be merged into a single use case, or should the multiplicity of scenarios be preserved?
Possible Resolutions:
Status: Open
ISSUE:[UC-0-02:Terminology] Several subcommittee members have found the current document, and particularly the use case scenario diagrams, confusing in that they use either domain-specific terminology (e.g., "Web User", "Buyer") or vague, undefined terms (e.g., "Security Service.").
One proposal is to replace all such terms with a standard actor naming scheme, suggested by Hal Lockhart and adapted by Bob Morgan, as follows:
A counter-argument is that abstraction at this level is the point of design and not of requirements analysis. In particular, the real-world naming of actors in use cases makes for a more concrete goal for other subcommittees to measure against.
Another proposal is, for each use case scenario, to add a section that maps the players in the scenario to one or more of the actors called out above.
Possible Resolutions:
Status: Open
ISSUE:[UC-0-02:Arrows] Another problem brought up is that the use case scenarios have messages (arrow) between actors, but not much detail about the actual payload of the arrows. Although this document is intended for a high level of analysis, it has been suggested that more definite data flow in the interaction diagrams would make them clearer.
UC-1-08:AuthZAttrs, UC-1-09:AuthZDecisions, and UC-1-11:AuthNEvents all address this question to some degree, but this issue is added to state for a general editorial principle for the document.
Possible Resolutions:
Status: Open
ISSUE:[UC-1-01:Shibboleth] The Shibboleth security system for Internet 2 (http://middleware.internet2.edu/shibboleth/index.shtml) is closely related to the SAML effort. An attempt has been made to address the requirements and design of Shibboleth in the SAML requirements document to allow implementation of SAML to be part of, or at least interoperable with, Shibboleth implementations.
In particular, the following issues have been introduced to address Shibboleth requirements:
If these issues, along with the straw man 2 document, have addressed the requirements of Shibboleth, then the subcommittee can address each issue on its own, rather than Shibboleth as a monolithic problem.
Possible Resolutions:
Status: Voted, Resolution 1 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 6 |
| Resolution 2 | 0 |
| Abstain | 3 |
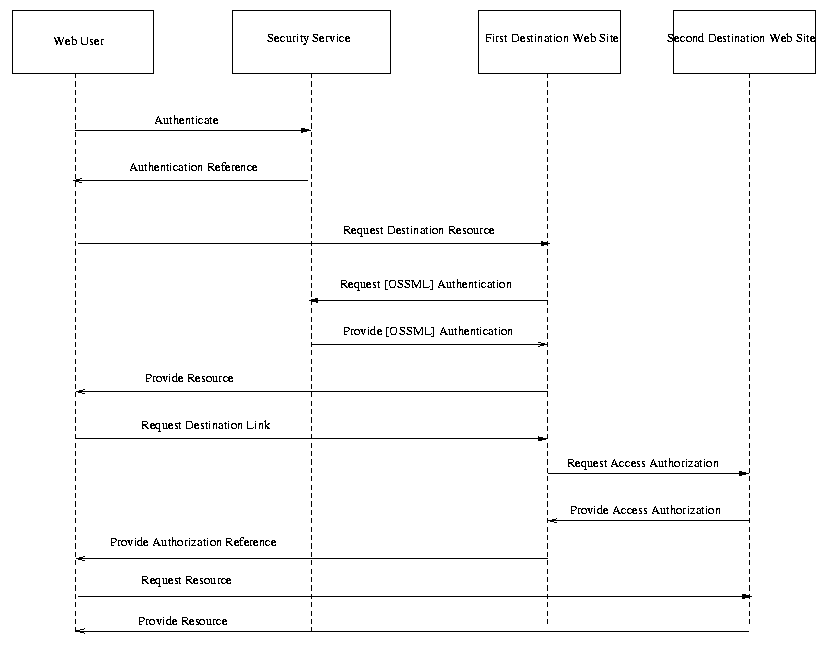
ISSUE:[UC-1-02:ThirdParty] Use case scenario 3 (single sign-on, third party) describes a scenario in which a Web user logs in to a particular 3rd-party security provider which returns an authentication reference that can be used to access multiple destination Web sites. Is this different than Use case scenario 1 (single sign-on, pull model)? If not, should it be removed from the use case and requirements document?
As written, the use case is not truly different from use case scenario 1. However, if the use case scenario is expanded to include multiple destination sites, the importance of this use case becomes more apparent.
The following edition to the single sign-on, third party use case scenario would be added:
In this single sign-on scenario, a third-party security service provides authentication assertions for the user. Multiple destination sites can use the same authentication assertions to authenticate the Web user. Note that the first interaction, between the security service and the first destination site, uses the pull model as described above. The second interaction uses the push model. Either of the interactions could use a different single sign-on model.

Fig. X. Single Sign-on, Third-Party
Security Service
Steps:
Possible Resolutions:
Status: Voted, Resolution 1 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 7 |
| Resolution 2 | 2 |
| Abstain | 0 |
ISSUE:[UC-1-03:ThirdPartyDoable] Questions have arisen whether use case scenario 3 is doable with current Web browser technology. An alternative is using a Microsoft Passport-like architecture or scenario.
It seems that at least one possible solution for the third-party security system exists -- that each destination site pass the authentication assertion from the third party security service to the next destination site, just as in peer source and destination scenarios such as use case scenarios 1 and 2.
Therefore, it seems that the scenario is at least theoretically implementable. It will be up to the other subcommittees and implementors of the standard to decide on how to define that implementation.
Possible Resolutions:
Status: Voted, Resolution 2 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 2 |
| Resolution 2 | 8 |
| Abstain | 0 |
Bob Blakley noted, "I think the proposed implementation only works if you follow direct links, and not if you pick destinations from a history list, use bookmarks, etc..."
ISSUE:[UC-1-04:ARundgrenPush] Anders Rundgren has proposed on security-use an alternative to use case scenario 2 (single sign-on, push model). The particular variation is that the source Web site requests an authorization profile for a resource (e.g., the credentials necessary to access the resource) before requesting access.
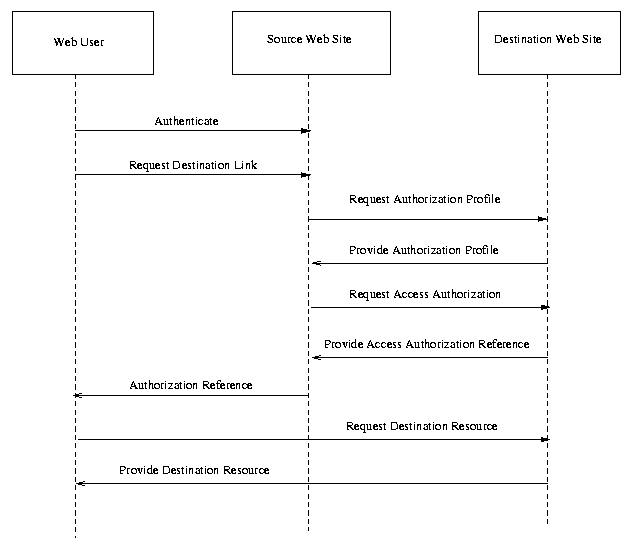
Fig X. Single Sign-on, Alternative Push
Model.
Possible Resolutions:
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 0 |
| Resolution 2 | 3 |
| Resolution 3 | 6 |
| Abstain | 0 |
Bob Blakley noted, "I can't really see how to do this without significant changes to the current link resolution architecture of web sites -- specifically without making sure both source and destination are expecting to have to handle this flow."
ISSUE:[UC-1-05:FirstContact] A variation on the single sign on use case that has been proposed is one where the Web user goes directly to the destination Web site without authenticating with a definitive authority first.
A single sign-on use case scenario would be added as follows:
In this single sign-on scenario, the user does not first authenticate with their home security domain. Instead, they go directly to the destination Web site, first. The destination site must then redirect the user to a site they can authenticate at. The situation then continues as if in a single sign-on, push model scenario.
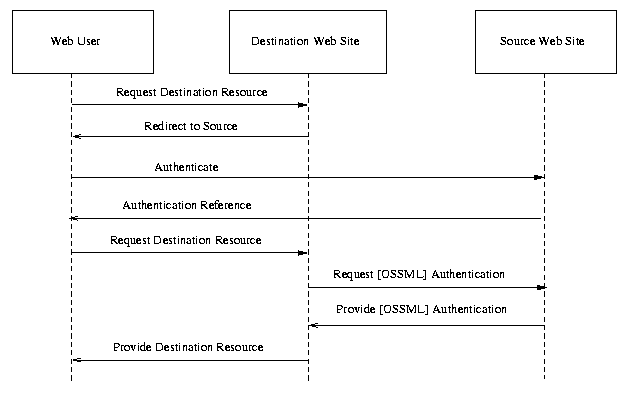
Single Sign-on, Alternative Push Model
Steps:
Possible Resolutions:
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 6 |
| Resolution 2 | 3 |
| Abstain | 0 |
Bob Blakley said, " I agree that servers will have to do this, but it can easily be done by writing HTML with no requirement for us to provide anything in our specification."
ISSUE:[UC-1-06:Anonymity] What part does anonymity play in SAML conversations? Can assertions be for anonymous parties? Here, "anonymous" means that an assertion about a principal does not include an attribute uniquely identifying the principal (ex: user name, distinguished name, etc.).
A requirement for anonymity would state:
[CR-1-06-Anonymity] SAML will allow assertions to be made about anonymous principals, where "anonymous" means that an assertion about a principal does not include an attribute uniquely identifying the principal (ex: user name, distinguished name, etc.).
Possible Resolutions:
Status: Voted, Resolution 1 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 9 |
| Resolution 2 | 0 |
| Abstain | 0 |
ISSUE:[UC-1-07:Pseudonymity] What part do pseudonyms play in SAML conversations? Can assertions be made about principals using pseudonyms? Here, a pseudonym is an attribute in an assertion that identifies the principal, but is not the identifier used in the principal's home domain.
A requirement for pseudonymity would state:
[CR-1-07-Pseudonymity] SAML will allow assertions to be made about principals using pseudonyms for identifiers.
Possible Resolutions:
Status: Voted, Resolution 1 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 7 |
| Resolution 2 | 2 |
| Abstain | 0 |
In support of Resolution 1, while voting, Bob Blakley said, "I'm really ambivalent about this. At an implementation level AND at a specification level, I can't see how a pseudonym should differ from a 'real' name. If it shouldn't, then we have no work to do. However, we should at least discuss the issue."
ISSUE:[UC-1-08:AuthZAttrs] It's been pointed out that the concept of an "authentication document" used in the use case and requirements document does not clearly specify the inclusion of authz attributes. Here, authz attributes are attributes of a principal that are used to make authz decisions, e.g. an identifier, or group or role membership.
Since authz attributes are important and are required by [R-AuthZ], it has been suggested that the single sign-on use case scenarios specify when authz assertions are passed between actors.
Possible Resolutions:
Status: Voted, Resolution 1 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 9 |
| Resolution 2 | 0 |
| Abstain | 0 |
ISSUE:[UC-1-09:AuthZDecisions] The current use case and requirements document mentions "Access Authorization" and "Access Authorization References." In particular, this data is a record of a authorization decision made about a particular principal performing a particular action on a particular resource.
It would be more clear to label this data as "AuthZ Decision Documents" to differentiate from other AuthZ data, such as AuthZ attributes or AuthZ policy. To this point, the mentions of "access authorization" would be changed, and a new requirement would be added as follows:
[CR-1-09-AuthZDecision] SAML should define a data format for recording authorization decisions.
Possible Resolutions:
Status: Voted, Resolution 1 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 8 |
| Resolution 2 | 0 |
| Abstain | 1 |
ISSUE:[UC-1-10:UnknownParty] The current straw man 2 document does not have a use case scenario for exchanging data between security services that are previously unknown to each other. For example, a relying party may choose to trust assertions made by an asserting party based on the signatures on the AP's digital certificate, or through other means.
The following use case scenario would illustrate using assertions from an unknown party.
In this scenario, an application service provider has a policy to allow access to resources for all full-time students at accredited 4-year universities and colleges. It would be difficult for the application service provider to maintain agreements with hundreds of such organizations in order to verify assertions made by those parties. Instead, it chooses to check the key of the asserting party to ensure that the asserting party is a 4-year university.
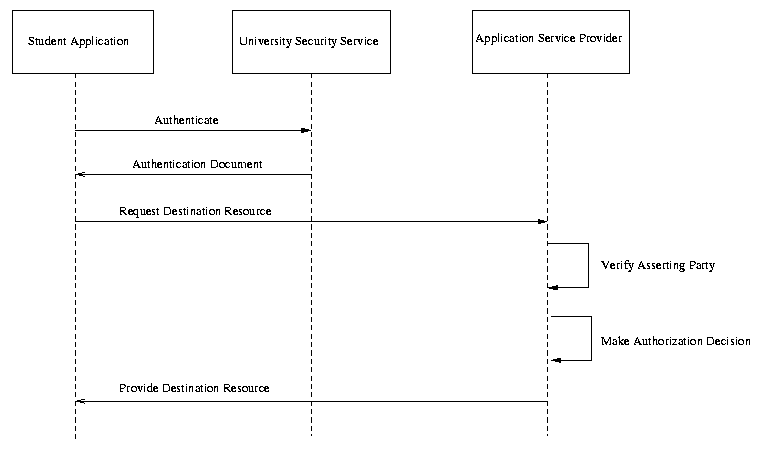
Fig X. Unknown Partner
Steps:
Possible Resolutions:
Status: Voted, Resolution 2 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 2 |
| Resolution 2 | 7 |
| Abstain | 0 |
In voting for resolution 2, Bob Blakley said, " I think this overspecifies behavior... both the 'interesting' flows in the diagram here are from the Application Service Provider to *itself*. Why should we tell the A.S.P. how to make trust decisions about assertions?"
ISSUE:[UC-1-11:AuthNEvents] It is not specified in straw man 2 what authentication information is passed between parties. In particular, specific information about authn events, such as time of authn and authn protocol are alluded to but not specifically called out.
The use case scenarios would be edited to show when information about authn events would be transferred, and the requirement for authn data would be edited to say:
[CR-1-11-AuthN] SAML should define a data format for authentication assertions, including descriptions of authentication events.
Possible Resolutions:
Status: Voted, Resolution 1 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 9 |
| Resolution 2 | 0 |
| Abstain | 0 |
ISSUE:[UC-1-12:SignOnService] Bob Morgan suggests changing the title of use case 1, "Single Sign-on," to "Sign-on Service."
Possible Resolutions:
Status: Open
ISSUE:[UC-1-13:ProxyModel] Irving Reid suggests an additional use case scenario for single sign-on, based on proxies.
A scenario would be added to the document as follows:
Scenario X: Single Sign-on, Proxy Model
In this model, the user authenticates to a proxy and then sends a request, including credentials, to the proxy. The proxy generates OSSML assertions, attaches them to the request, and forwards the request to the destination web site. The destination web site replies to the proxy, and the proxy forwards the reply back to the client.
In this model, the user authenticates to a proxy and then sends a request, including credentials, to the proxy. The proxy generates OSSML assertions, attaches them to the request, and forwards the request to the destination web site. The destination web site replies to the proxy, and the proxy forwards the reply back to the client.
Alternatively, the initial message from the client to the proxy could include both the authentication credentials and the request rather than having a separate round-trip for authentication.
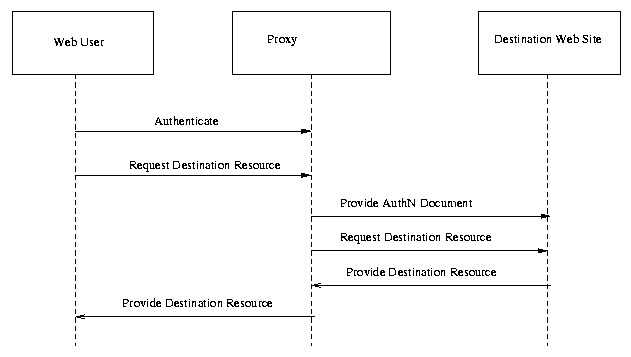
Fig X. Single Sign-on, Proxy Model
Steps:
There are two sub-variants to this use case: In some cases the proxy will return OSSML tokens of some sort to the client, and the client will use those tokens (most likely in the form of HTTP cookies) to make subsequent requests within the single-sign-on session. In the other variant, the proxy has an existing session mechanism with the client. In that case, the proxy can store the OSSML tokens and transparently attach them to subsequent requests within that session.
Possible Resolutions:
Status: Open
ISSUE:[UC-2-01:AddPolicyAssertions] Some use cases proposed on the security-use list (but not in the straw man 1 document) use a concept of a "policy document." In concept a policy document is a statement of policy about a particular resource, such as that user "evanp" is granted "execute" privileges on file "/usr/bin/emacs." Another example may be that all users in domain "Acme.com" with role "backup administrator" may perform the "shutdown" method on resource "mail server," during non-business hours.
Use cases where policy documents are exchanged, and especially activities like security discovery as in UC-4-04:SecurityDiscovery, would require this type of assertion. If these use cases and/or services were adapted, the term "policy document" should be used. In addition, the following requirement would be added:
[CR-2-01-Policy] SAML should define a data format for security policy about resources.
In addition, the explicit non-goal for authorization policy would be removed.
Possible Resolutions:
Status: Open
ISSUE:[UC-2-02:OutsourcedManagement] A use case scenario provided by Hewlett Packard illustrates using SAML enveloped in a CIM/XML request. Should this scenario be included in the use case document?
The use case would be inserted as follows (some editing for clarity):
This scenario shows an enterprise A that has outsourced the management of its network devices to a management service provider B. Management messages are exchanged using CIM/XML over HTTP. (CIM or Common Information Model, is a management standard being developed by the Distributed Management Task Force - http://www.dmtf.org/, an XML DTD for CIM has been defined.)
Suppose the operator, Joe, wants to invoke the StopService method. This will be executed by the XML/CIM agent on the managed device, if authorized.
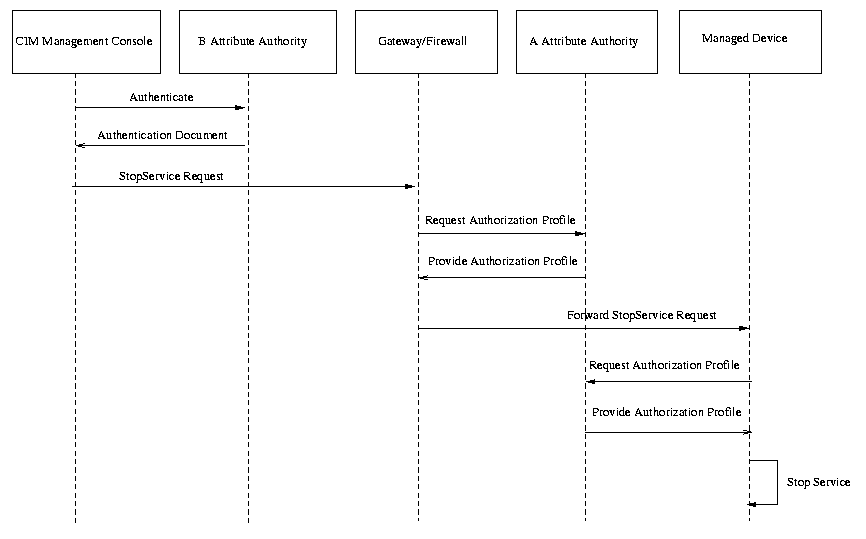
Fig X. Outsourced Management.
Steps:
Status: Open
ISSUE:[UC-2-03:ASP] A use case scenario provided by Hewlett Packard illustrates using SAML for a secure interaction between an application service provider (ASP) and a client. Should this scenario be included in the use case document?
The use case would be inserted as follows (some editing for clarity):
In this scenario an ASP, A, is providing an application (possible examples could be a word processor or an ERP application) to users in another enterprise, B. A VPN (for example IPSEC) is used to provide a secure end-to-end tunnel between the client and server.
A major difference between this scenario and the outsource management service scenario is that all assertions are "pulled" in this scenario. This means the assertions are not attached to application messages; instead they must be retrieved either directly from the attribute authority, or a repository. For example, once the client has been authenticated, the SAML evaluation engine in the server needs to retrieve the SAML assertions issued by A and B. This will involve making a request to a repository inside B, traversing both A and B's firewall as shown in the diagram. Similarly the SAML engines in the gateway and client will have to retrieve assertions issued by both authorities.
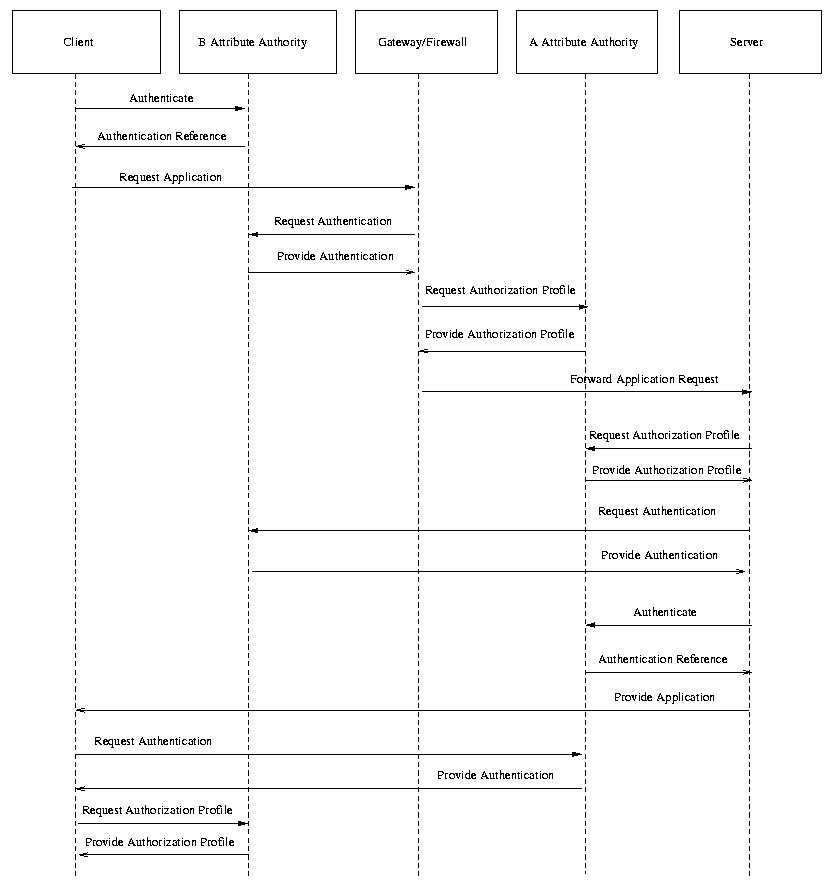
Fig X. Application Service Provider.
Steps:
Status: Open
ISSUE:[UC-2-04:HealthCare] A request for a use case focussing on health care and particularly HIPPA has been made in the Security Services TC. Should such a use case scenario be added to the use case document? What are the particulars of HIPPA and how are they different from other use cases?
Status: Open
ISSUE:[UC-2-05:B2B Transaction via an e-marketplace or trading hub] Zahid Ahmed proposes the following additional use case scenario for inclusion in the use case and requirements document.
A B2B Transaction involving buyers and suppliers that conduct trade via an e-marketplace that provides trading party authentication and authorization services, and other business services, in support of secure transaction and routing of business document exchanges between trading parties.
Steps:
Possible Resolutions:
Status: Open
ISSUE:[UC-2-06:B2B Transaction using different messaging and application protocols] Zahid Ahmed has proposed that the following use case scenario be added to the use case and requirements document.
A B2B Document Exchange Transaction that involves two trading parties such that sending trading party (e.g., Buyer) uses one messaging and transport protocol (e.g., OBI) and receiving party (e.g., Supplier) uses a another messaging/transport protocol (e.g., ebXML). A B2B transaction service must provide relevant security interoperability services as part of its general messaging and application interoperability mechanism.
Steps:
Possible Resolutions:
Status: Open
ISSUE:[UC-2-07:B2B Transaction over multiple e-marketplace or trading hubs/portals] Zahid Ahmed proposes the following use case scenario for inclusion in the document. This use case/issue is a variant of ISSUE# [UC-2-05].
In this scenario the transacting trading parties are members of different e-marketplaces or trading communities. To support B2B transactions between trading parties of different e-markletplaces, the e-marketplaces will provide secure interconnectivity between the set of trading hubs involved in the transaction between the transaction parties. In this manner e-marketplaces will act as trusted intermediaries between transacting trading parties.
Steps:
Possible Resolutions:
Status: Open
ISSUE:[UC-2-08:ebXML] Maryann Hondo proposed this use case scenario for inclusion in the use case document. (Note that an interaction diagram illustrating this use case still must be developed, to replace the current diagram. Also, the steps involved should be brought in line with other use case scenarios in the use case and requirements document.)
Use Case Scenario X: ebXML
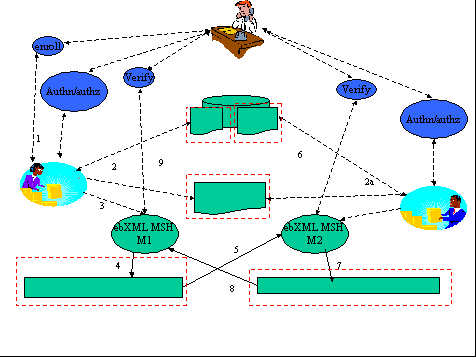
Fig X. ebXML
Steps:
Potential Resolutions:
Status: Open
ISSUE:[UC-3-1:UserSession] Should the use cases of log-off and timeout be supported? These result in the notion of session management. Advantage: Allows complete web user experience across multiple web sites. If not done as part of this specification, then some other body or work will have to standardize this functionality. Disadvantage: More complex than just passing authentication references between source and destination. Will slow down Technical committees work on specification of authentication/authorization only queries.
Candidate Requirement:
[CR-3-1-UserSession] SAML shall support web user session(s).
The following use case scenario would be added to the use case and requirements document.
A Single Sign-on and hand-off
Note that this is a duplicate of Oasis security Services Scenario #1
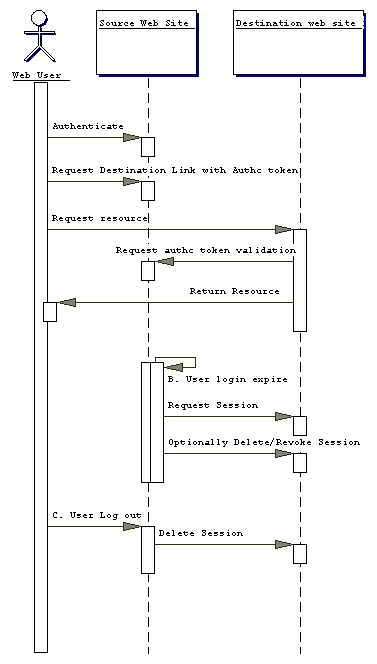
Fig X. Single Sign-on, User Session.
Steps:
Timeout
Logout
Possible Resolutions:
Status: Voted, Resolution 1 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 8 |
| Resolution 2 | 2 |
| Abstain | 0 |
In voting for resolution 1, Jeff Hodges added, "rationale: if there's these "assertions" floating about between various entities that serve to assert the identity of some particular entity, there's notions of "validity time period" (however implemented), and there's notions of "state" relative to the asserted identity, then I feel what we have here meets the definition of a "session", and we ought to use that term (and really figure out what all the implications are)." He also attached the following URLs:
http://foldoc.doc.ic.ac.uk/foldoc/foldoc.cgi?query=session&action=Search
http://foldoc.doc.ic.ac.uk/foldoc/foldoc.cgi?query=state
ISSUE:[UC-3-02:ConversationSession] Is the concept of a session between security authorities separate from the concept of a user session? If so, should use case scenarios or requirements supporting security system sessions be supported? [DavidO: I don't understand this issue, but I have left in for backwards compatibility]. [DarrenP: I think this issue arose out of a misunderstanding/miscommunication on the mailing list and has been resolved. This is more of a formality to vote this one to a closed status.]
Possible Resolutions:
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 5 |
| Resolution 2 | 5 |
| Abstain | 0 |
ISSUE:[UC-3-03:Logout] Should SAML support transfer of information about logout (e.g., a principal intentionally ending a session)? [DavidO: Isn't this covered in UC-3-1? I've kept here for backwards compatibility]
Candidate Requirement:
[CR-3-3-Logout] SAML shall support web user logout.
Possible Resolutions:
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 5 |
| Resolution 2 | 5 |
| Abstain | 0 |
In voting for resolution 2, Jeff Hodges added, "rationale: I believe this is subsumed within the topic of [UC-3-1:UserSession] and we should deal with it explicitly in that context."
ISSUE:[UC-3-6:Destination Logout] Should logging out of a destination web site be supported? Advantage: allows web sites control over their local domain, current model implemented on the web. Disadvantage: potentially more interactions between source and destination web sites
Candidate Requirement:
[CR-3-6-Destination Logout] SAML shall support logout at destination web sites
Possible Resolutions:
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 4 |
| Resolution 2 | 5 |
| Abstain | 1 |
ISSUE:[UC-3-7:Logout Extent] What is the impact of logging out at a destination web site?
Possible Resolution:
Status: Voted, Resolution 1 Carries
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 7 |
| Resolution 2 | 0 |
| Resolution 3 | 1 |
| Abstain | 2 |
Jeff Hodges, abstaining, said, "rationale: needs clarification. E.g. BobB's point in Group3VoteBlakley.html should be considered."
ISSUE:[UC-3-04:StepUpAuthn] "Step-up" authentication is when a receiving party refuses to accept an authentication from an authenticating party and asks for a higher level of authentication. For example, the RP can refuse password authn and require certificate authn. Should SAML support step-up authentication? Should a use case be developed illustrating step-up authn?[DavidO: I don?t think this is applicable to the session requirements, but I?ve kept here for backwards compatibility].
Possible Resolutions:
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 5 |
| Resolution 2 | 4 |
| Abstain | 1 |
ISSUE:[UC-3-05:SessionTimeout] Should timeout be supported?
Candidate requirement:
[CR-3-5-Timeout] SAML shall support timeout of a user log-on.
Possible Resolutions:
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 6 |
| Resolution 2 | 4 |
| Abstain | 0 |
In voting for resolution 2, Jeff Hodges added, "rationale: I believe this is subsumed within the topic of [UC-3-1:UserSession] and we should deal with it explicitly in that context."
Bob Blakley said, "However I believe that the phrasing of the requirement is wrong. I think what we should support is expiration of assertions. Timeout is an action a receiving system implements based on observing that an assertion has timed out."
ISSUE:[UC-3-8:Destination Timeout] Should timing out of a session at a destination web site be supported?
Candidate requirement:
[CR-3-8-DestinationTimeout] SAML shall support destination web site timeout.
Possible Resolutions:
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 4 |
| Resolution 2 | 6 |
| Abstain | 0 |
In voting for resolution 2, Jeff Hodges added, "rationale: I believe this is subsumed within the topic of [UC-3-1:UserSession] and we should deal with it explicitly in that context."
Bob Blakley said, "I don't feel that I understand well enough what we'd consider doing here to express an opinion yet."
ISSUE:[UC-4-01:SecurityService] Should part of the use case document be a definition of a security service? What is a security service and how is it defined?
Status: Open
ISSUE:[UC-4-02:AttributeAuthority] Should a concept of an attribute authority be introduced into the SAML use case document? What part does it play? Should it be added in to an existing use case scenario, or be developed into its own scenario?
Status: Open
ISSUE:[UC-4-03:PrivateKeyHost] A concept taken from S2ML. A user may allow a server to host a private key. A credentials field identifies the server that holds the key. Should this concept be introduced into the SAML use case document? As a requirement? As part of an existing use case scenario, or as its own scenario?
Status: Open
ISSUE:[UC-4-04:SecurityDiscover] UC-1-04:ARundgrenPush describes a single sign-on scenario that would require transfer of authorization data about a resource between security zones. Should a service for security discovery be part of the SAML standard?
Possible Resolutions:
Status: Open
ISSUE:[UC-5-03:AuthNThrough] All the scenarios in Straw Man 1 presume that the user provides authentication credentials (password, certificate, biometric, etc) to the authentication system out-of-band.
Possible Resolutions (not mutually exclusive):
[NO-Authn] Authentication methods or frameworks are outside the scope of SAML.
Status: Voted, Resolution 1 Fails, Resolution 2 Passes, Resolution 3 No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 For | 1 |
| Resolution 1 Against | 10 |
| Resolution 2 For | 10 |
| Resolution 2 Against | 1 |
| Resolution 3 For | 7 |
| Resolution 3 Against | 4 |
| Abstain | 0 |
NOTE: resolutions for this issue were voted on separately.
ISSUE:[UC-5-02:SASL] Is there a need to develop materials within SAML that explore its relationship to SASL [SASL]?
Possible Resolutions:
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 | 3 |
| Resolution 2 | 5 |
| Abstain | 2 |
[ISSUE:[UC-5-01:AuthNProtocol] Straw Man 1 explicitly makes challenge-response authentication a non-goal. Is specifying which types of authn are allowed and what protocols they can use necessary for this document? If so, what types and which protocols?
As written, this issue covers a lot of ground. [UC-5-03:AuthNthrough] covers the core issue of the removal of all considerations of modeling authentication methods within SAML, which need not be discussed further in 5-01.
There is an aspect of these requirements that has been discussed and noted as important on the list. There is a need for describing different forms of credentials (name-password, public key, X509 certificates etc) within OSSML. In this sense there is a connection to the different "permitted forms of authn" [2] and OSSML.
REFERENCES: I believe these requirements are consistent with or can be derived from Nigel's suggestion [1] but is perhaps closer to the current style of specification in Strawman 2. It also reflects the discussion in [2] and [3].
[1] http://lists.oasis-open.org/archives/security-use/200102/msg00029.html
[2] http://lists.oasis-open.org/archives/security-use/200102/msg00038.html
[3] http://lists.oasis-open.org/archives/security-use/200102/msg00064.html
Possible Resolutions (not mutually exclusive):
"Challenge-response authentication protocols are outside the scope of the SAML"should be removed from the Strawman 3 document.
[CR-5-01-1-StandardCreds] SAML should provide a data format for credentials including those based on name-password, X509v3 certificates, public keys, X509 Distinguished name, and empty credentials.
[CR-5-01-2-ExtensibleCreds] SAML The credentials data format must support extensibility in a structured fashion.
Status: Voted, No Conclusion
Voting Results
| Date | 23 Feb 2001 |
| Eligible | 18 |
| Resolution 1 For | 8 |
| Resolution 1 Against | 3 |
| Resolution 2 For | 8 |
| Resolution 2 Against | 3 |
| Abstain | 0 |
In voting for resolution 2, Bob Blakley said, "My thinking here is that we need to provide a way to assert what mechanism was used to authenticate the user (e.g. certificate-based authentication) and what the user's authenticated credential resulting from that authentication (e.g. X.509 cert) was. I'm still nervous about allowing the VALUE of the password to be used as credential information as in S2ML, but I do understand why this was done and that it's useful."
ISSUE:[UC-6-01:XMLProtocol] Should mention of a SOAP binding in the use case and requirements document be changed to a say "an XML protocol" (lower case, implying generic XML-based protocols)? Or "XML Protocol", the specific W3 RPC-like protocol using XML (http://www.w3.org/2000/xp/)?
Status: Open
ISSUE:[UC-7-01:Enveloping] SAML data will be transferred with other types of XML data not specific to authn and authz, such as financial transaction data. What should the relationship of the documents be?
Note that of the solutions below, 2. is more useful when the conversation is mostly an SAML conversation, such as for single sign-on. 3. is more useful for conversations that are mostly "other," such as XML-based server-to-server commerce.
Possible Resolutions:
Status: Open
ISSUE:[UC-8-01:Intermediaries] The use case scenarios in the S2ML 0.8a specification include one where an intermediary passes an S2ML message from a source party to a destination party. What is the part of intermediaries in an SAML conversation? Can intermediaries add, subtract, or alter data in an SAML message? Should a use case scenario involving a 3rd-party intermediary be included in the use case and requirements document?
Status: Open
ISSUE:[UC-9-02:PrivacyStatement] Important private data of end users should be shared as needed between peers in an SAML conversation and protected entirely from hostile 3rd parties. In addition, the user should have control over what data is exchanged. How should the requirement be expressed in the use case and requirements document? Should a use case scenario illustrating privacy protection be provided?
One statement suggested by Bob Morgan is as follows:
[CR-9-02-3-DisclosureMorgan] SAML should support policy-based disclosure of subject security attributes, based on the identities of parties involved in an authentication or authorization exchange.
[CR-9-02-2-DisclosureBlakley] SAM should support *restriction of* disclosure of subject security attributes, *based on a policy stated by the subject*. *This policy might be* based on the identities of parties involved in an authentication or authorization exchange.
Status: Open
ISSUE:[UC-9-01:RuntimePrivacy] Should protecting the privacy of the user be part of the SAML conversation? In other words, should user consent to exchange of data be given at run time, or at the time the user establishes a relationship with a security system?
Status: Open
ISSUE:[UC-10-01:Framework] Should SAML provide a framework that allows delivery of security content negotiated out-of-band. A typical use case is authorization extensions to the core SAML constructs. The contra-position is to rigidly define the constructs without allowing extension.
Possible Resolutions:
Status: Open
ISSUE:[UC-11-01:AuthzUseCase] The use case scenarios outlined in straw man 2 include explicitly only authn use cases. Should a use case featuring an authz conversation, such as a policy enforcement point (PEP) querying a policy decision point (PDP) for authorization for a user to execute an action?
The use case would be included as follows:
Scenario N: Authorization Service
This use case illustrates an authorization service that provides authorization checks for resource access. This authorization service is expected to operate within a single security domain, where the owner of the resource also controls the policies at the Policy Decision Point corresponding to those resources.
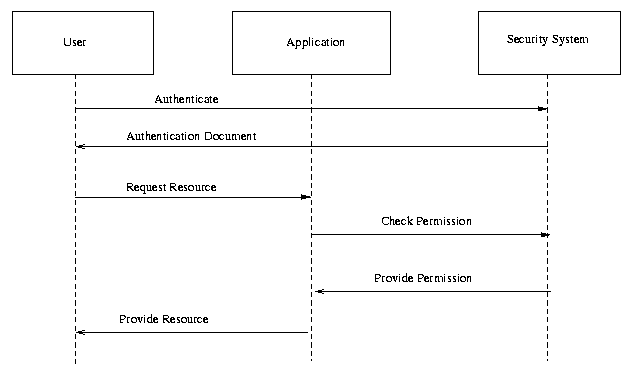
Fig X. Authorization Service.
Steps:
Possible Resolutions:
Status: Open
ISSUE:[UC-11-02:AuthzFirstContact] A second scenario for the Authorization use case combines first contact single-sign-on (UC-1-05:FirstContact), authentication (UC-5-01:AuthNProtocol) and authorization.
Scenario N+1: Authorization Service, First Contact with Authentication
In this scenario, the client makes contact only with the application; there is not a separate authentication phase between the user and the security system.
Steps:
Possible Resolutions:
Status: Open
ISSUE:[UC-12-01:Encryption] UC-9-02:PrivacyStatement addresses the importance of sharing data only as needed between security zones (from asserting party to relying party). However, it is also important that data not be available to third parties, such as snoopers or untrusted intermediaries.
One possible solution for implementors is to use secure channels between relying party and asserting party. Another is to use encryption, either with a shared secret or with public keys.
Possible Resolutions:
Status: Open
ISSUE:[UC-13-01:Scalability] Bob Morgan brought up several "business requirements" on security-use. One was scalability. This issue is a placeholder for further elaboration on the subject.
A candidate requirement might be:
[CR-13-01-Scalability] SAML should be appropriate for high volume of messages, and for messages between parties made up of several physical machines.
Status: Open
ISSUE:[UC-13-02:EfficientMessages] Philip Hallam-Baker's core assertions requirement document included several requirements that were efficiency-oriented. When that requirement document was merged into Straw Man 2, the efficiency requirements were excluded.
One such requirement was:
[CR-13-02-EfficientMessages] Should support efficient message exchange Integrity checks such as digital signature can add excessive overhead to messages.
Potential Resolutions:
Status: Open
ISSUE:[UC-13-03:OptionalAuthentication] Philip Hallam-Baker's core assertions requirement document included several requirements that were efficiency-oriented. When that requirement document was merged into Straw Man 2, the efficiency requirements were excluded.
One such requirement was:
[CR-13-03-OptionalAuthentication] Authentication should be optional To Satisfy [R-EfficientMessages] Messages may omit authentication altogether.
Potential Resolutions:
Status: Open
ISSUE:[UC-13-04:OptionalSignatures] Philip Hallam-Baker's core assertions requirement document included several requirements that were efficiency-oriented. When that requirement document was merged into Straw Man 2, the efficiency requirements were excluded.
One such requirement was:
[CR-13-04-OptionalSignatures] Signatures should be optional To Satisfy [R-EfficientMessages] Messages may use a shared secret and Message Authentication code for Authentication in place of digital signature.
Status: Open
ISSUE:[UC-13-05:SecurityPolicy] Bob Morgan proposed a business-level requirement as follows:
[CR-13-05-SecurityPolicy] Security measures in [OSSML] should support common institutional security policies regarding assurance of identity, confidentiality, and integrity.
Potential Resolutions:
Status: Open
ISSUE:[UC-13-06:ReferenceReqt] Bob Morgan has questioned requirement [R-Reference] in that it is not specific enough. in particular, he said:
"Goal [R-Reference] either needs more elaboration or (likely) needs to be dropped. What is a 'reference'? It doesn't have a standard well-understood security meaning nor is it defined in the glossary. This Goal seems to me to be making an assumption about a low-level mechanism for optimizing some of the transfers."
One possible, more specific elaboration might be:
[CR-13-06-1-Reference] SAML should define a data format for providing references to authentication and authorization assertions. Here, a "reference" means a token that may not be a full assertion, but can be presented to an asserting party to request a particular assertion.
[CR-13-06-2-Reference-Message] SAML should define a message format for requesting authentication and authorization assertions using references.
[CR-13-06-2-Reference-Size] SAML references should be small. In particular, they should be small enough to be transfered by Web browsers, either as cookies or as CGI parameters.
Potential Resolutions:
Status: Open